Alright everyone, buckle up! Let’s talk about this world where super-powerful quantum computers meet cybersecurity. Imagine a future where our most sensitive data is absolutely, positively untouchable. We’re talking about a digital realm where communication is so secure, even the sneakiest cyber bad guys can’t eavesdrop. Think about online banking without a shred of worry, government secrets locked tighter than a drum, and personal information truly being personal. That’s our utopian vision – a world where quantum tech has actually boosted our digital defenses to levels we can barely dream of today.
Now, speaking of today, did you know that in 2023, * there were a whopping 42,155 publications related to Quantum Technology (QT)? That’s a massive amount of brainpower focused on this stuff, showing just how much momentum, this field has!
*(Source: Report on quantum technology monitor, April 2024 by McKinsey)
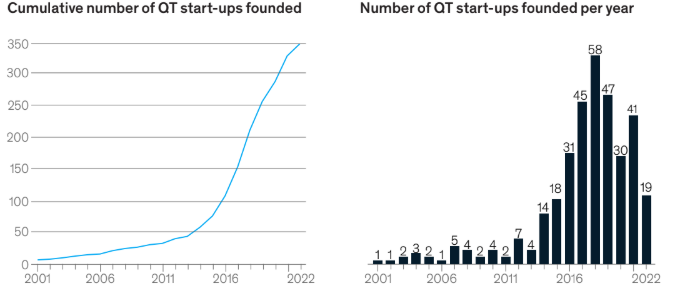
But let’s not get ahead of ourselves. Right now, quantum computing presents some serious head-scratches for cybersecurity
- Our current encryption is at risk: The big worry is that powerful quantum computers will be able to crack the encryption methods that keep our online lives secure today. *Think of algorithms like RSA (Rivest–Shamir–Adleman) and SSL/TLS (Secure Sockets Layer/Transport Layer Security). These rely on mathematical problems that are super hard for regular computers but could be a walk in the park for a quantum computer.
Reason: Quantum computers can perform multiple calculations simultaneously due to the principles of quantum physics. This gives them the potential to break down the complex math behind current encryption much faster than classical computers.
*(Source: A game plan for quantum computing report by McKinsey) - “Harvest now, decrypt later” attacks are a concern: Bad actors could be scooping up encrypted data now, knowing they might be able to decrypt it once they have access to sufficiently powerful quantum computers in the future.
Reason: Data that needs to remain secret for a long time is particularly vulnerable because the threat of quantum decryption isn’t immediate but is looming.
- We might not be ready in time: Developing and implementing new, quantum-resistant security measures takes time and effort. There’s a real risk that quantum computers will advance faster than our ability to secure our systems against them.
Reason: The development of quantum computers is progressing rapidly, and creating “quantum-proof” cryptography is a complex challenge involving research, standardization, and widespread adoption.
But hold on, we truly believe that our vision of a quantum-secure future is achievable! The key is to tackle these problems head-on, and thankfully, smart folks around the world are already on it. If we focus our efforts and resources in the right places, we can absolutely build a digital world that’s even more secure in the quantum age.
So, how do we get there? Here are some potential solutions and things we should be doing
- Develop and implement Post-Quantum Cryptography (PQC): This is all about creating new encryption algorithms that are designed to be resistant to attacks from both classical and quantum computers.
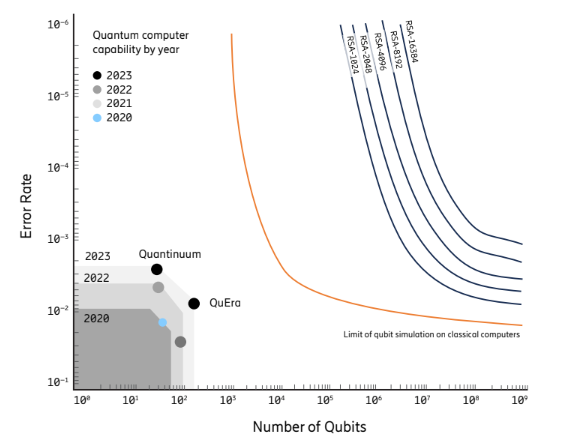
Organizations like NIST (National Institute of Standards and Technology) are already working on standardizing these new algorithms. We need to make sure these standards are robust and that industries start adopting them ASAP. It shows the development of quantum computers by the number of qubits and their error rate, highlighting the gap we need to bridge before they become a serious threat to current cryptography. This helps visualize the urgency of PQC.
- Explore and implement Quantum Key Distribution (QKD). This technology uses the principles of quantum mechanics to establish secure communication channels for exchanging encryption keys. Any attempt to eavesdrop on a QKD transmission would leave a detectable trace, making it a very secure way to share secret keys.
While it might require new hardware and infrastructure, QKD offers a fundamentally different and potentially ultra-secure approach to key exchange.
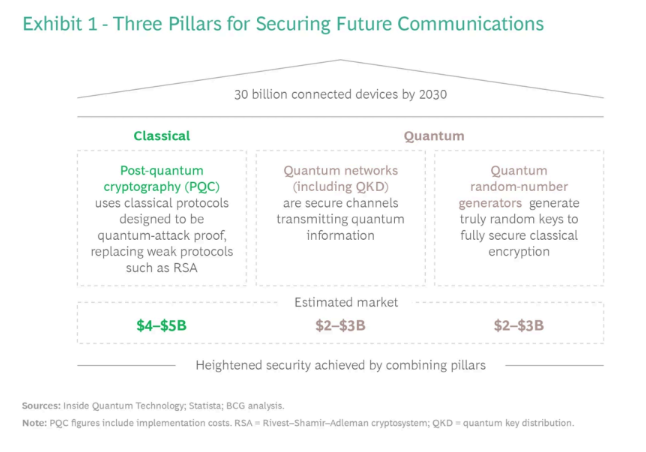
- Embrace “crypto-agility.”: This means building systems that can quickly and easily switch between different encryption algorithms. This way, if a vulnerability is found in a PQC algorithm in the future, we can rapidly move to a more secure alternative.
- Raise awareness and educate: Businesses and individuals need to understand the quantum threat and the importance of preparing for it. This includes training cybersecurity professionals in quantum-resistant techniques.
- Government and industry collaboration is crucial: Governments need to support research and development in quantum security and work with industries to facilitate the adoption of new standards and technologies.
- Consider hybrid approaches: Combining classical and quantum security measures might offer the most robust protection in the near term.
- Start assessing your data’s lifespan and sensitivity: Organizations should identify data that needs long-term protection and prioritize its migration to quantum-safe methods.
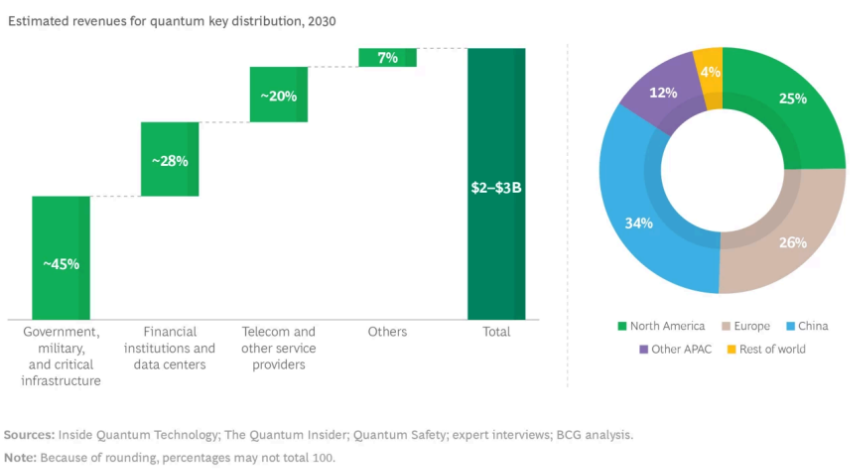
What are your thoughts on all of this? Are you feeling optimistic or worried about the cybersecurity implications of quantum computing? Let’s hear your perspective!
As we step into the quantum age, cybersecurity is no longer just an IT concern—it’s a trust and brand reputation issue. The same way data needs to evolve for tomorrow’s threats, your brand and marketing strategies must evolve to signal security, relevance, and innovation. At Zamun, we blend cutting-edge insights with creative strategy to position your brand as future-ready—from storytelling that builds trust, to messaging that reflects your commitment to data privacy and tech-forward thinking. To know more about how we can take your organization to a higher orbit, visit Our Services Page or drop in an email to connect.)
FAQs
Not yet—but it’s on the horizon. While current quantum machines aren’t powerful enough to break encryption, development is moving fast. It’s a “prepare now” situation.
Any data that needs to stay secure long-term—like government records, financial data, or personal health info—is vulnerable to “harvest now, decrypt later” attacks.
PQC is the next-gen encryption designed to withstand attacks from both classical and quantum computers. Think of it as future-proofing your data.
PQC upgrades existing algorithms for post-quantum safety, while QKD is a totally new way of securely sharing encryption keys using quantum mechanics.
Glossary
SSL: SSL, or Secure Sockets Layer, is a protocol that encrypts communication between a web server and a browser, ensuring secure data transmission over the internet. It’s a foundational protocol for secure websites and online transactions
TLS: Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over a computer network. It’s widely used for applications like web browsing (HTTPS), email, and other online interactions to ensure the confidentiality and integrity of data transmission
Sources
- Report on quantum technology monitor, April 2024 by McKinsey
- Article on game plan for quantum computing report by McKinsey, 2024
- Report on Impact of quantum computing on 5/6G security by Ericsson, 2023
- Article: Are you ready for Quantum communication by BCG, 2023
- What is quantum computing?, 2025 by McKinsey
